It is rare at Logistics Viewpoints (LV) that we would do more than reference a few sentences from another publication. However, I believe that Bloomberg Businessweek’s recently published article titled The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies is thought provoking and (potentially) consequential enough to warrant an entire post. I recommend that LV readers set aside some time to read the entire article for themselves. But in the meantime, I would like to take this opportunity to summarize some key points and provide a supply chain perspective.
We have written a number of times on Logistics Viewpoints about managing the extended supply chain, including global trade management, supply chain visibility, traceability, and overall integrity. Of course, these concepts don’t necessarily capture the issue of government espionage efforts. That is something best left for government entities with 3 letter acronyms. However, this (alleged) incident is an example of how complex and difficult to manage today’s international supply chains have become.
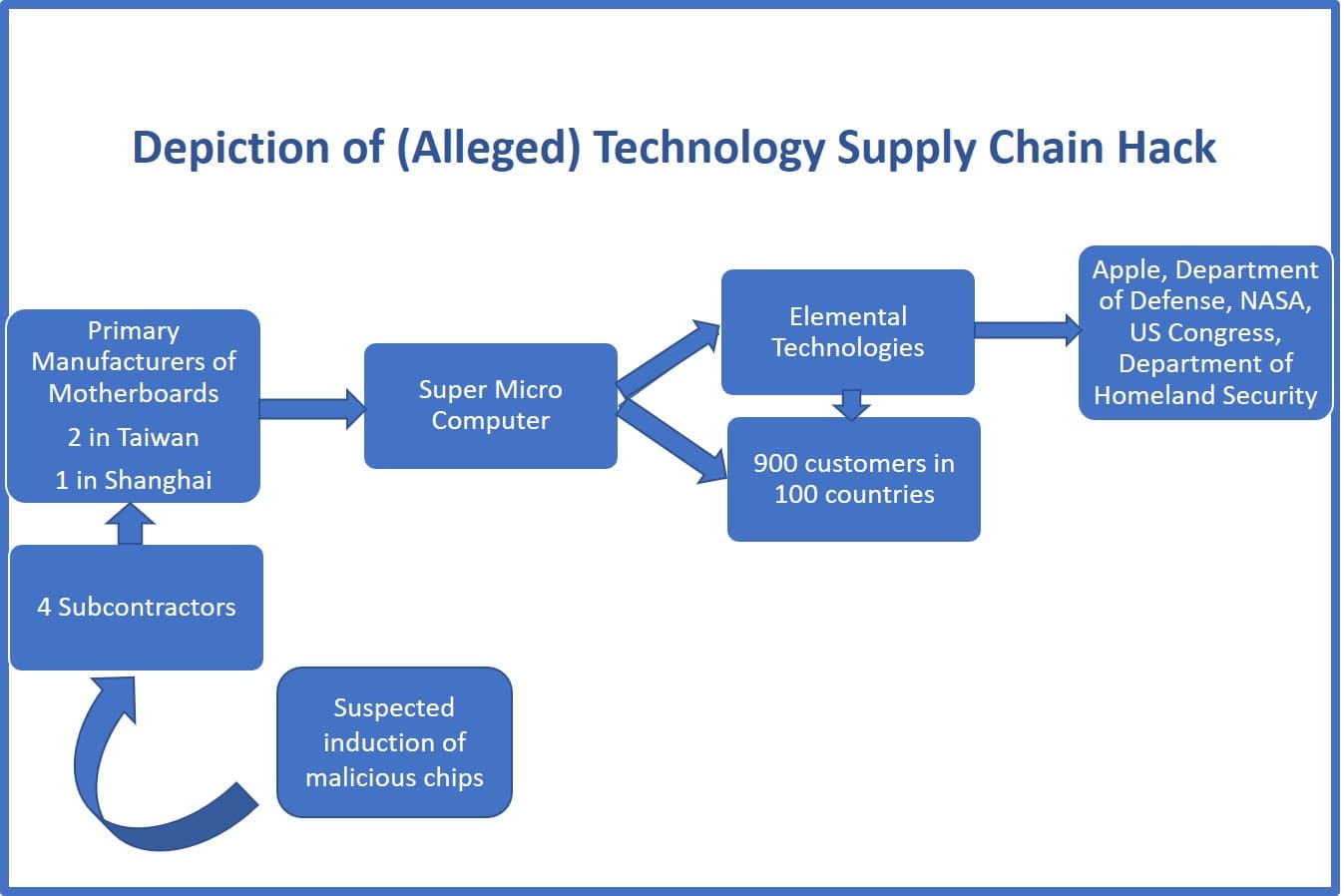
The Bloomberg article, written by Jordan Robertson and Michael Riley, lays out the supply chain of Elemental Technologies, a provider of video compression, processing, and formatting solutions. It’s worth noting that all companies mentioned in the article deny the issues or occurrences mentioned (hence my use of the term “alleged”). The journey begins with Amazon’s research into Elemental as a possible acquisition candidate. Amazon’s due diligence included an in-depth review of the company’s servers, which uncovered a tiny microchip on the boards of the devices that were not part of the original design. Amazon subsequently reported its findings to the US Government, which set off substantial interest and concern. And for good reason, as Elemental’s servers are in use at the US Department of Defense, US Navy, NASA, the Department of Homeland Security, and both houses of Congress. Ongoing investigations by the US Government determined that the inserted chips allowed attackers to access the networks in which the compromised servers were present.
Where Supply Chain Traceability Comes in Play
Elemental Technologies’ servers were assembled by Super Micro Computer, a San Jose, CA company. Super Micro, in my opinion, is the epicenter of this story. As the authors state in the article, “Unlike software-based hacks, hardware manipulation creates a real-world trail. Components leave a wake of shipping manifests and invoices. Boards have serial numbers that trace to specific factories.” And this supply chain event data, often used in supply chain visibility applications, was used by authorities to trace the invasive chips back to their source. They worked their way back from Super Micro in the US to 3 primary manufacturers, two in Taiwan and one in Shanghai, responsible for producing its motherboards. From there the US intelligence community used other means to trace the chips back to four factories that were subcontractors of the primary manufacturers of the motherboards. It is at these factories that agents of the People’s Liberation Army (again “allegedly”) infiltrated the manufacturing process to insert the chips into the motherboards.
Final Word
The four subcontractors at which the infiltration by the People’s Liberation Army is attributed are four steps back (excluding logistics partners) into the extended supply chain. This example of an alleged breakdown in the integrity of the Super Micro Computer extended supply chain is clearly an extreme case. However, the value of traceability in the effort to determine the source of corruption and the effects on customers and the business of Super Micro Computer are substantial. Supply chain visibility and global trade management applications offer a platform for real-time insights and retro-active analysis of supply chain events, required documentation, and other essential insights that assist in an efficient and effective management of one’s extended supply chain. Does your organization have detailed data of your extended supply chain at its fingertips? If not, maybe its time to evaluate the business case for establishing the required processes and infrastructure to develop this ability.